A lot of things are changing in the online world these days at a very fast pace. Especially the trend regarding privacy concerns that has widely been started with the GDPR in Europe, now makes its way to the rest of the world. As a result more and more browser vendors are starting to put privacy at their top priority. This results in a lot of changes on how browsers restrict cookies which we will have a deeper look at.
Note: if you think it’s a smart idea to circumvent cookies by using browser local storage, please be aware that browser vendors are also imposing restrictions on them, so this won’t be a long-lasting solution. In addition local storage is a same origin solution, which means you will have different storages for www.recolize.com and tool.recolize.com.
The goal of browser privacy
Apple’s Safari was one of the first browsers enabling more privacy-friendly settings by default. With their so-called “Intelligent Tracking Prevention” logic (ITP) in 2017 they started to limit tracking across different sites. Lately in 2020 also they are the ones pushing mobile advertisers to find new solutions for example by restricting the use of the App Advertising ID on iPhones in iOS 14.
Other browser vendors like Google Chrome or Mozilla Firefox are also already doing similar approaches or looking into it.
Basically what all measures by the browser vendors have in common is to limit tracking of their users across different sites. Therefore there are 3 basic concepts that all browsers more or less do follow:
- Drastically limiting expiry time of third-party cookies
- Prohibiting cookies in unsecure contexts
- Limiting expiry times of content created in JavaScript context (e.g. cookies or browser local storage)
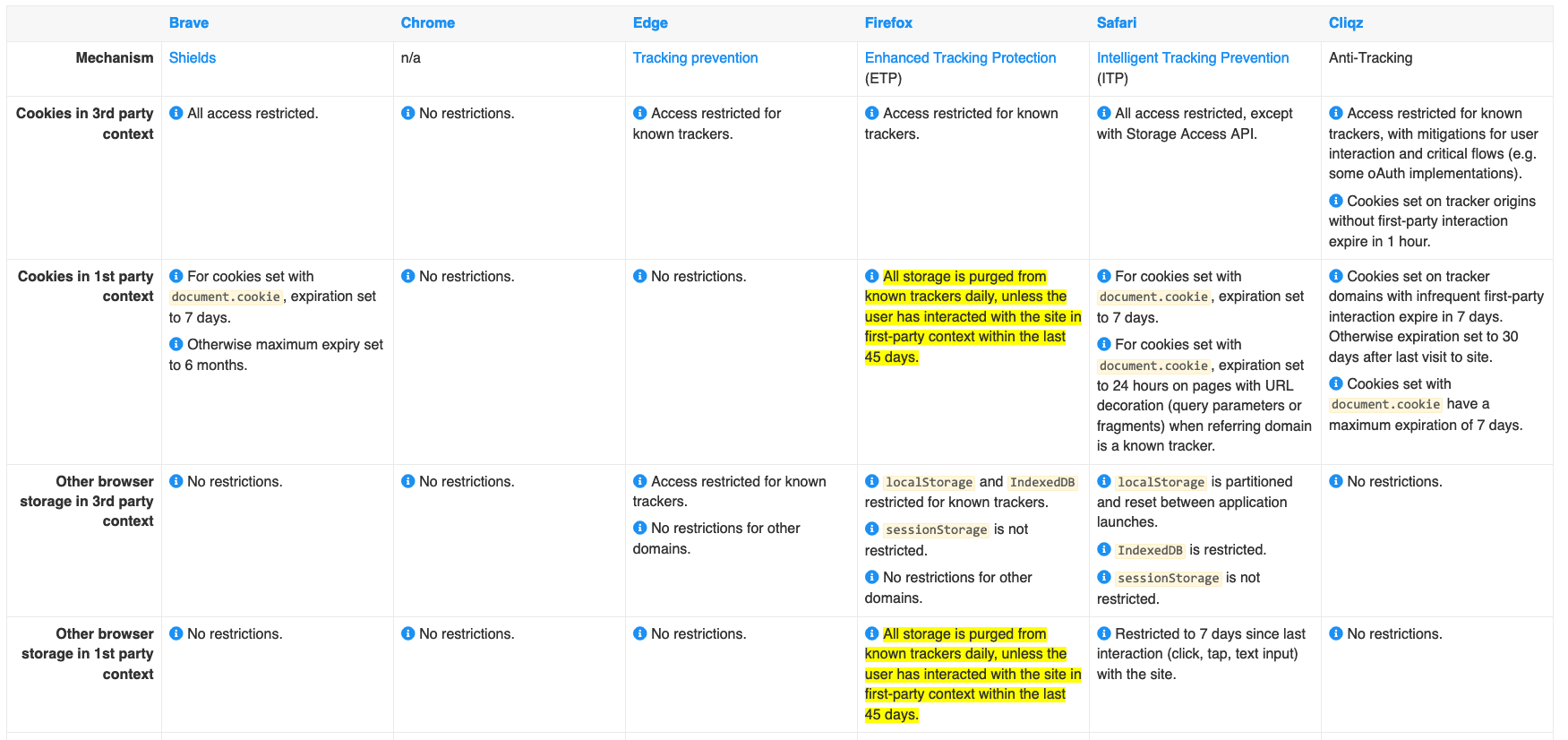
As it is very difficult to stay on top on how the different browsers restrict cookies and local storage, the website cookiestatus.com is a very good information source:
What to do with your cookies now ?
Basically there are 3 important cookie attributes:
HttpOnly: this cookie attribute guarantees that the cookie cannot be access by JavaScript at all.Secure: this cookie attribute transmits cookies only in case that you are accessing the URL via HTTPSSameSite:
The attribute can have the valuesStrict,LaxorNonethat tell the browser in which context the cookie is allowed to be accessed, with the first one being restricted to the same site requests. Whereas the latter has no restrictions for cross site requests, that means the cookie will be attached to any request which imposes the security risk of CRSF.
For a detailed explanation see the excellent post on the Google Blog and the Mozilla documentation.
With the information derived from above we can conclude the following measures for your cookies:
- Use first-party cookies whereever possible
- Session cookies, e.g. for your shopping cart, should be set to
HttpOnly,SecureandSameSite=None. This prevents the browsers from blocking unsecure cookies while still allowing cookies after being redirected from external links so that the shopping cart remains available. - Session cookies e.g. for your secure admin interface should be set to
HttpOnly,SecureandSameSite=Strict. In contrast to the session cookies above this does not allow requests from non-first party context to steal your session. - all other cookies, especially the ones required by JavaScript, should at least be set to
SecureandSameSite=None. If these cookies are created via JavaScript, the expiry time will be only 7 days e.g. in Safari browser in general.
Please also pay attention to the fact that browsers do have different default settings for cookies that are missing e.g. the SameSite attribute. Newer browser versions of Firefox and Chrome do set SameSite=Lax by default which could result in issues e.g. that your Magento shopping carts gets cleared after redirect from payment provider!
How to implement the cookie attributes in PHP?
So as written above to mitigate how browser restrict cookies, in most cases you are good to go if you set your cookies to Secure and SameSite=Lax. In PHP starting from 7.3 this can be done very easily by using the following method:
setcookie('cookie-name', 'value', [ 'secure' => true, 'samesite' => 'None' ]);
If you are using an older PHP version below 7.3 (which you obviously should not do from a security perspective) the method parameters are a little bit different and you have to “tweak” it a little bit like this:
setcookie('cookie-name', 'value', 0, '/; SameSite=Lax; Secure', '', true);
As many of our customers are still using the popular Magento 1 online shop software here is a small trick you can use:
Update Magento’s core_config_data table and set web/cookie/cookie_path value to /; SameSite=None; Secure
This is not a permanent solution, but it might be useful for a temporary workaround.
Of course this blog post can only highlight some changes of how browsers restrict cookies in 2020 and this is also subject to constant change. But you should have gotten a glimpse on where the trend goes and what to do to update your implementation.